- Exploring Data Type Categories
- Intro
- Seven types of NSM data are discussed in this lesson, including session data, full packet capture, transaction data, extracted content, alert data, statistical data, and metadata. Correlation of events between the various NSM data sets is also important.
- NSM Data
- 
- Geolocations, ip owner, reputation scores (metadata)
- 5-tuple most important (address:port)x2+protocol
-
- NSM Data Types
- Not really useful until correlated and analyzed.
- Session data (netflow, 5-tuple)
- Full packet capture (wiretap)
- Transaction data (daemon logs, accounting logs like on a linux box)
- Extracted data (email attachments, downloads, can be pulled/mined)
- Statistical data (baselines)
- Alert data (crystallized, usually starts analysis)
- Syslog (realtime push logs, filebeats on windows)
- Indicator of Compromise (IOC)
- Examples: IP of attacker can be correlated with other traffic, registry entries by a piece of malware.
- OpenIOC is an extensible XML schema that enables security professionals to describe the technical characteristics that identify a known threat, an attacker’s methodology, or other evidence of compromise.
- Network Time Protocol (NTP)
- NTP as useful for forensics and can be authenticated.
- Security Info and Event Management Systems
- The biggest SIEM deployment decision question you have to ask is, howdoes this technology help find incidents that you would not otherwise be able to find using existingtools?
- Reasons why?
- Security monitoring and incident response
- Anomaly detection
- Real-time rules-based alerts
- Data correlation
- Compliance or regulatory mandated logging and reporting
- Automated reports
- The statistical and mathematical correlation determinations are best handled by the SIEM. However, the logical correlation can really only be done well by a human brain. Example: sysadmin prescanning a host before using SCP (not actually an incident)
- Security Orchestration, Automation and Response
- SOAR automates information security event management processes and incident response procedures.
- A SOAR analyzes cyber threat intelligence (CTI) from external threat feeds.
- Example: Cisco SecureX
- Security, Orchestration and Automation, Automated Incident Response. + Threat Intelligence
- Security Onion Overview
- 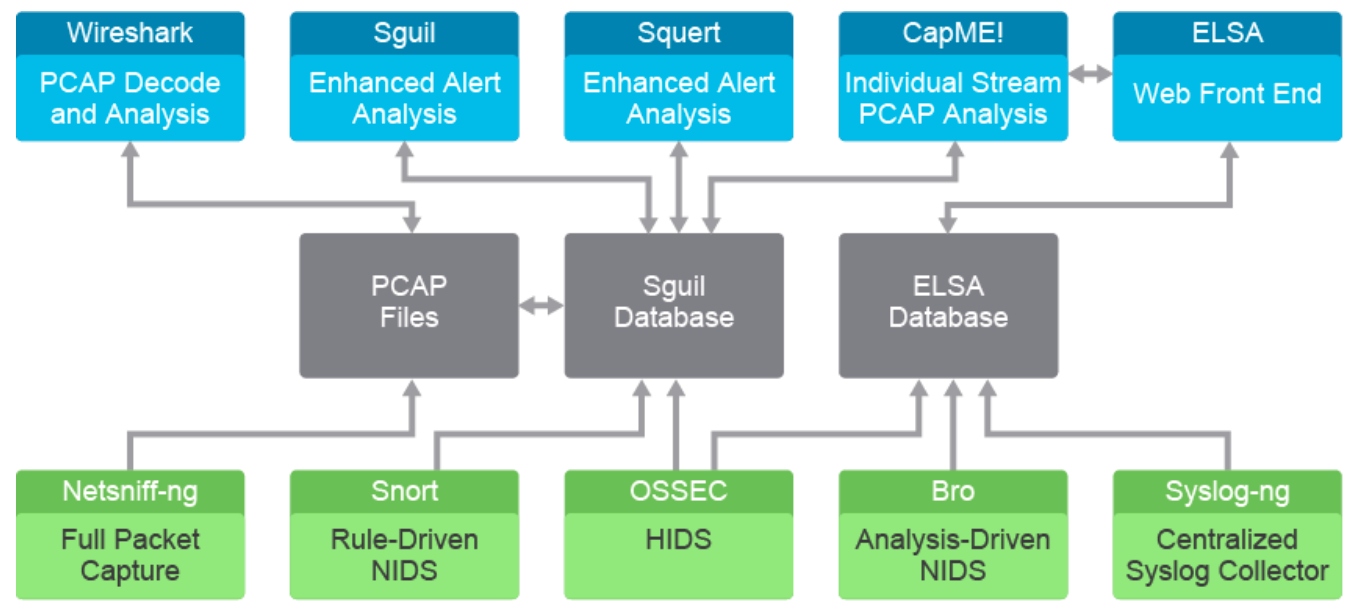
- Standalone, server-sensor (ssh tunnels to Pull data from sensors), Hybrid.
- Bro - network analysis. ELSA - syslog. Sguil - friendly GUI. Squert - webapp for Sguil dasta - visualization. Suricata - nextgen ids/ips. Snort - standard IPS, signatures, protocols, anomalies.
- Full Packet Capture
- Location - chokepoints like ingress at critical net locations
- Method
- Span, TAP, inline two interfaces
- SPAN least reliable
- TAP splits duplex to 2 simplex and does not guarantee compute will keep up. Taps also convenient if they have a fail open to wire speed.
- Inline can be a bottleneck but is most reliable - good if can forward at line speed.
- NIC config: must not enable offload capabilities (checksumming, segment etc.)
- 90% delete of oldest pcaps
- Packet Captures
- instant replay, in-depth packet level analysis, or sharing between analysts.
- netflow as alternative to excessive full pcap
- special concerns: ips of hosts maybe affected, the path used in the attack, the timeline of the attack.
- privacy concerns with raw data, for example exfiltrated by icmp
- Packet Capture Using Tcpdump
- Telnet, FTP, HTTP, and SNMPv1 and SNMPv2) send data in cleartext
- windump is a win version
- -n option prevents dns lookup of hostname
- -X hex, -XX ascii text mode, -w write, -r read
- Session Data
- 5-tuple, byte/packet count
- principle of limit redundancy, Bro can produce much more than session data. The analyst can configure it to produce session data, transaction data, extracted content, statistical data, metadata, and alert data.
- session data can be matched with suspicious ext ips, lateral movement and exfiltration ips
- Transaction Data
- Transaction data provides audit trails of client requests and server responses. ex. smtp, dhcp
- Some NSM tools can decode application protocols, recognize transactions within the live traffic, and produce transaction logs.
- Alert Data
- ids/ips distinction more on how deployed: portmirror/taps ids, inline without dropds, ids, inline with drop ips.
- pivoting to transaction data to see if attack actually hit target.
-
- Other Data Types
- Statistical data aggregates the individual events and provides summaries of the data.
- The summaries of statistical data can be used by the analyst to develop a clear and coherent picture that may not be discernable from examining individual events.
- Relevant queries against statistical data can answer certain questions. Two common queries are top reports and baseline graphs.
- Cisco Stealthwatch for baselines
- The concept of sliding window anomaly detection utilizes a baseline that is long enough to include the regularly recurring deviations but short enough to avoid legacy data patterns from long ago to distort current data patterns.
-
- Correlating NSM Data
- event correlation across multiple data types and data sources is critical to the network security analysis process.
- Infosec CIA
- Confidentiality prevents unauthorized disclosure of sensitive information. Encryptions can be used to ensure the confidentiality of the data transfers traversing across the network. Integrity prevents unauthorized modification of information, providing assurance of the accuracy of the information. Cryptographic hash functions (such as SHA-1 or SHA-2) can be used to provide data integrity. Availability is the prevention of loss of access to resources and information to ensure that information is available for use when it is needed. Methods that are used to protect against loss of availability include deploying fault tolerant systems, redundancies, and data backups.
- PII
- Examples of PII data include the following:
- Name, such as full name, maiden name, mother's maiden name
- Telephone numbers, including home, and mobile numbers
- Date and place of birth
- Passport number, social security number, driver license number
- Personal characteristics, including photographic image (especially of the face or other distinguishing characteristic), x-rays, fingerprints, or other biometric image or template data (for instance, retina scan, voice signature, and facial geometry)
- Regulatory Compliance
- PCI DSS, HIPAA, SOX, GDPR, PSI, FISMA, GLBA, PIPEDA, DPD, BASEII, DMCA Safe Harbor
- Intellectual Property
- “It’s identifying what you need to protect, determining who would benefit from taking it, understanding the vectors that can be used to compromise it, and then developing a defense commensurate with the value of the property.”
- Intellectual property has traditionally been defined as trademarks, copyrights, patents, and trade secrets for which a person or organization can claim exclusive ownership. But in today’s business world, that definition has expanded to include virtually any nonmaterial asset—whether owned in a strictly legal sense or not—that distinguishes a business and enables it to thrive and prosper. Cisco refers to these as information assets.
- Sales figures, design docs, customer lists, banking info, human capital.
- The most effective way to protect information assets is to carefully inventory what must be protected and identify how those assets relate to the people and processes that make up the business’ intricate skein of trust relationships.
- Zero trust, The emergence of the zero trust security model has also shifted the center focus of some security frameworks from securing the perimeter to protecting sensitive data such as the company’s information assets.
- Using NSM Tools to Analyze Data Categories
- malware-traffic-analysis.org for evil pcaps
- The Payload Security website https://www.hybrid-analysis.com/allows an analyst to upload a suspected file for analysis. Other web services such as virustotal.com
-